The Phenomenon of the Computer Underground
James Ullrey © 1998
When I was a graduate student at UC Davis I would work ten or twelve hours in the lab, and about 9 or 10 PM the rates would go down for my account on the UNIX systems and I would boogie on over to the computer center in the basement of Barrows Hall where the rows and rows of terminals would be lined up to link up to the PDP-11's, The Burroughs 6700 and the VAXen.
I was a computational chemist. I had learned how to invert matrices and had used that trick to write some code that would fit three points to a parabola.
After a sequence of events which is a long story(which has yet to be told and is a project in progress) I will direct you to the animations of my PhD research project results which were the result of using that trick.
There were games to play and beautiful women(UNIX Consultant) to fall in love with.
The games were "The Collasul Cave", text based games that had you solve puzzels and create maps. I have the Crowther Woods vending machine maze implemented in html
elsewhere on this site.
Then came dungeon which was similar but different. This made its way into the commercial mainstream in the form of the Zork Trilogy
Rogue came next. This one had you fighting the monsters as you solved levels and picked up weapons and scrolls, magic rings and potions. The object of the game was to rescue the Amulet of Yendor. The closest I came to experiencing fear came as I encountered at level ten my first Troll, the first bad ass motherfucker you meet in this game.
There was one UNIX consultant named Peter who, legend has said, put up a trojan horse on the machine of the supervisor, stole his password and captured the source code for Rogue, hacked it so that he could hack around the wizards password and gain debug status for the game.
Peter was the first hacker that I knew.
Everybody knew that I was quite fond of Cindy. I was able to let her know straight away that I was married and had two kids. She would let me play Rogue on her account. Last saw her in Irvine in '87 when I gave a paper on the subject of chemical physics at the ACS Pac Con.
Then there were the virus writers. These were like hackers, but destructive.
Then there was Cliff Stoll's book, "The Cuckoo's Egg". It was so fascinating that I read it in just a few sessions.
Then there was the Computer Underground Digest(cud), posted regularly to Berkeley Macintosh Users Group(BMUG) that alerted me to the existence of the underground.
cud reported an incident that occurred in the Washington DC Mall. A group of young folks were rousted from a public place by Mall Security Forces at the behest of the Secret Service. The group rousted was the local 2600 Meeting. I found out that there was a 2600 meeting in San Francisco. Meets the first Friday of every month in the court in front of Mrs. Fields Cookies in 4 Embarcadero Plaza.
I started going.
Should you fear hackers?
Rumors: there are 60,000 - 100,000 hackers and hacker wannabes.
Getting to the bottom of the cyber attacks
US computer security called a Critical Mess
Number 1 Enemy of the Pentagon, Datastream Cowboy
Massive hack attacks occur Analyzer and friends bring down 10,000 pentagon computers. Analyzer gets busted. Dyslexic teenager goes on to career as advertising personality at age 18.5 --
'Analyzer' makes hack claims.
Pentagon gets wake up call. Sorting out the hacks and the hackers. News analysis from two journalistic perspectives.
Not a conspiracy say experts.
Hack attacks seen as increasing,
Fed security expert speaks out on hacks
Rumors: Your 14 year old can fix the Pentagons computer vulnerability.
Military computers broken into by MOD gang.
This is what they found
Military secrets(?) stolen by MOD.
AntiOnline author threatened for MOD coverage
A different perspective on the threats.
A story on the above posted letter by John Glave of Wired News.
MSNBC has story
MSNBC story on unsecured pentagon computers.
Now hiring hackers
CyberGangs
HackerStopers intrusion detection tools.
MOD steals info from NASA site about the intrusion detection software
Where do they get their tools? Mudge, cryptanalysist extraordinary
Shoddy Windows NT security gives hacker rock star Mudge of the l0pht a place in history
mudge testifies before the US Senate
Bruce Schneier gets coverage for exposing security holes in NT VPN protocol
All of a sudden hackers are heros.
Hacker wars: Self styled computer security expert recruits Cryptik of the 505 Gang to be host with his box cryptotek.happyhacker.org and becomes lightning rod for the wrath of the hacker community and gets subjected to 1000 hacker attacks per day. Started about March 27th.
Upstream providers take collateral damage.
Coming soon: Monitoring the progress of the games
Recent misstracking of a satellite over China has aroused suspicions in the hacker community that cDc is up to their old tricks.
Certain high placed individuals claim that the threat in the story FBI "Cries Wolf" Over Hackers is underestimated.
Se7en, the hacker who came in from the cold.
Se7en's vigilante action.
Who is Kevin Mitnick?
Colleges seek ways to handle hacker attacks.
Teens a threat says Pentagon.
Teenage crackers break into computer systems in India's Bhabha Atomic Research Centre as a protest against the impending nuclear arms race in the Asian subcontinent and are targeting Pakistani computers.
Antionline site reports details of the MilW0rm groups attacks of the India Nuclear research facility
[Hacked sites]
The week of 980621-980628:
John Vranesevich reports the latest antics of a group called
Chad - Computer Hackers Against Despotism.
http://www.icas.spear.navy.mil
Highest Priority
Clueless congress critters about to make a serious mistake WIPO or World Intellectual Property Organization. John does a better job of describing the peril.
The following phone script was taken from the web page of the Electronic Freedom Foundation. I am sure they will not mind that I repeat it here.
Call your congress person.
Better yet, ask to speak to the legislator's technology & intellectual property staffer.
Legislative staffer: Hello, Representative Lastname's office.
You: I'm calling to urge Representative Lastname to support, at the June 17 Commerce Committee markup, amendment of H.R. 2281, the "WIPO Copyright Treaties Implementation Act", with the language in the more carefully crafted alternative, H.R. 3048, the Boucher/Campbell "Digital Era Copyright Enhancement Act". I am extremely concerned about H.R. 2281's effects on privacy.
Additionally, the bill's anti-circumvention provision is overbroad. Both bills have the same goals, but the provisions of H.R. 3048 replacing those of 2281 will protect intellectual property while also protecting privacy, security, science and free speech. At bare minimum, I ask Representative Lastname to help ensure that the WIPO bill is amended to criminalize infringing behavior instead of trying to ban technology that simply "could" be used for infringement even if not intended for such abuse. Thank you.
Staffer: OK, thanks. [click]
A quote is appropriate here: When i dig it out of the place where it is stored I will add it to the commentary.
MilW0rm continues with the attack on the India Pakistan nuclear situation by essentially adding grafitti to 300 web sites.
How do you know if you have been hacked?
This is reported on pointed out on Wired News The Wired News story gives more details, including the fact that the attack was against a virtual web hosting company in the UK.
First reported in Wired News a Chinese hacking group called Yellow Pages aligns itself with the Cult of the Dead Cow and claims to have disabled temporarily a Chinese satellite. Text of the interview
Hackers demonstrate in front of offices of Miramax, the producers of the movie Takedown, based somewhat on the book by the same name by John Markoff chronicling the hunt and capture of Kevin Mitnick. Mitnick has been held without bail for three years while being prevented from participating in his defense by the circumstances of his incarceration.
Unusual Suspects a story in Corporate Report on intrusion testing.
Legion of the Underground(LOD) claim control of your TV
Wired News reports US DOD blames rootshell for a spate of recent(unsuccessful) attacks on military sites. The article goes on to say that commercial and non commercial intrusion detection systems play an important part in the defense of important military sites.
Fighting hackers with freeware, reported by news.com, enlightens readers to the existence of the SANS Institute, an educational group for systems administrators and security specialists.
"Honey Pot" model set to lure hackers into sting operation.
The race to add intrusion detection.
Axent Technologies announced NetRecon, software for probing networks for vulnerabilities, both from the internet and from internal users, to hacker attacks.
recent pentium chip hacked, says 'bill sux'
UNIX Security
Q: Why is the subject, security, necessary?
A: in a word, hackers!
Background info: http://users.lmi.net/~ullrey/dark.html
Old school hackers vs. new school hackers and crackers.
What kinds.
script kiddies. exploits for fame
infosec community
intruder community
the invisible ones
the bank caper, where millions of $ were diverted to St. Petersburg Russia, all but $400,000 recovered.
New group it seems every week.
MOD: 10,000 military WinNT machines the week Bill Gates testified before congress
milW0rm: The India Nuclear Research Facility. Later, 300 web sites defaced.
LOD: We control your TV.
How do they do it?
go to http://www.rootshell.com
if you know the name of an exploit, you can search for it. If you don't, rootshell maintains a history of recent search keys, so you can look at what someone else looked for.
smurf4.c
targa.c - runs on Linux, SunOS and BSD
incorporates in one program recent exploits such as:
bonk route & daemon9 route is editor of Phrack and daemon9 is author
jolt
land
nestea
newtear route & daemon9
syndrop
teardrop route & daemon9
winnuke
InfoSec and Intruder Communities. They write them
Invisible: $10,000,000 Russian bank caper
Cliff Stoll's The Cuckoo's Egg
What to do about it.
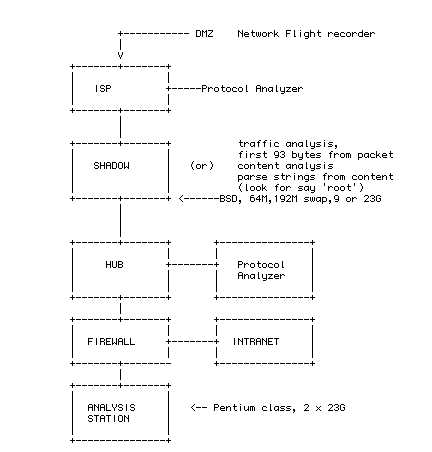
Firewalls: packet-filters and proxy servers
Intrusion Detection Devices
CIDER CIDER
Cooperative
Intrusion
Detection
Evaluation
Response
tcpdump.tar.Z
libpcap.tar.Z <--- how UNIX sys gets network info from the
kernel
both from ftp://ftp.ee.lbl.gov
get tcpslice.tar.Z as well


